Cyber Security Scams and How to Protect Yourself
Phishing
Phishing attacks use email or malicious websites to infect your machine with malware and viruses in order to collect personal and financial information. Cybercriminals attempt to lure users to click on a link or open an attachment that infects their computers, creating vulnerability to attacks. Phishing emails may appear to come from a real financial institution, e-commerce site, government agency, or any other service, business, or individual. The email may also request personal information such as account numbers, passwords, or Social Security numbers. When users respond with the information or click on a link, attackers use it to access users’ accounts.
HOW CRIMINALS LURE YOU IN
The following messages from the Federal Trade Commission’s OnGuardOnline are examples of what attackers may email or
text when phishing for sensitive information:
- “We suspect an unauthorized transaction on your account. To ensure that your account is not compromised, please click
the link below, and confirm your identity.” - “During our regular verification of accounts, we couldn’t verify your information. Please click here to update and verify your
information.” - “Our records indicate that your account was overcharged. You must call us within 7 days to receive your refund.”
- To see examples of actual phishing emails, and steps to take if you believe you received a phishing email, please visit “
SIMPLE TIPS TO SECURE IT.
- Play hard to get with strangers. Links in email and online posts are often the way cybercriminals compromise your
computer. If you’re unsure who an email is from—even if the details appear accurate—do not respond, and do not click on
any links or attachments found in that email. Be cautious of generic greetings such as “Hello Bank Customer,” as these are
often signs of phishing attempts. If you are concerned about the legitimacy of an email, call the company directly. - Think before you act. Be wary of communications that implore you to act immediately. Many phishing emails attempt
to create a sense of urgency, causing the recipient to fear their account or information is in jeopardy. If you receive a
suspicious email that appears to be from someone you know, reach out to that person directly on a separate secure
platform. If the email comes from an organization but still looks “phishy,” reach out to them via customer service to verify
the communication. - Protect your personal information. If people contacting you have key details from your life—your job title, multiple email
addresses, full name, and more that you may have published online somewhere—they can attempt a direct spear-phishing
attack on you. Cyber criminals can also use social engineering with these details to try to manipulate you into skipping
normal security protocols. - Be wary of hyperlinks. Avoid clicking on hyperlinks in emails and hover over links to verify authenticity. Also ensure that
URLs begin with “https.” The “s” indicates encryption is enabled to protect users’ information. - Double your login protection. Enable multi-factor authentication (MFA) to ensure that the only person who has access to
your account is you. Use it for email, banking, social media, and any other service that requires logging in. If MFA is an
option, enable it by using a trusted mobile device, such as your smartphone, an authenticator app, or a secure token—a
small physical device that can hook onto your key ring. Read the Multi-Factor Authentication (MFA) How-to-Guide for more
information. - Shake up your password protocol. According to NIST guidance, you should consider using the longest password or
passphrase permissible. Get creative and customize your standard password for different sites, which can prevent cyber
criminals from gaining access to these accounts and protect you in the event of a breach. Use password managers to
generate and remember different, complex passwords for each of your accounts. Read the Creating a Password Tip Sheet
for more information. - Install and update anti-virus software. Make sure all of your computers, Internet of Things devices, phones, and tablets are equipped with regularly updated antivirus software, firewalls, email filters, and anti-spyware.
Strong Passwords
Creating a strong password is an essential step to protecting yourself online. Using long and complex passwords is one of
the easiest ways to defend yourself from cybercrime. No citizen is immune to cyber risk, but #BeCyberSmart and you can
minimize your chances of an incident.
SIMPLE TIPS TO SECURE IT.
Creating a strong password is easier than you think. Follow these simple tips to shake up your password protocol:
- Use a long passphrase. According to NIST guidance, you should consider using the longest password or passphrase
permissible. For example, you can use a passphrase such as a news headline or even the title of the last book you read.
Then add in some punctuation and capitalization. - Don’t make passwords easy to guess. Do not include personal information in your password such as your name or pets’
names. This information is often easy to find on social media, making it easier for cybercriminals to hack your accounts. - Avoid using common words in your password. Substitute letters with numbers and punctuation marks or symbols. For
example, @ can replace the letter “A” and an exclamation point (!) can replace the letters “I” or “L.” - Get creative. Use phonetic replacements, such as “PH” instead of “F”. Or make deliberate, but obvious misspellings, such
as “enjin” instead of “engine.” - Keep your passwords on the down-low. Don’t tell anyone your passwords and watch for attackers trying to trick you into
revealing your passwords through email or calls. Every time you share or reuse a password, it chips away at your security by
opening up more avenues in which it could be misused or stolen. - Unique account, unique password. Having different passwords for various accounts helps prevent cyber criminals from
gaining access to these accounts and protect you in the event of a breach. It’s important to mix things up—find easy-toremember ways to customize your standard password for different sites. - Double your login protection. Enable multi-factor authentication (MFA) to ensure that the only person who has access to
your account is you. Use it for email, banking, social media, and any other service that requires logging in. If MFA is an
option, enable it by using a trusted mobile device, such as your smartphone, an authenticator app, or a secure token—a
small physical device that can hook onto your key ring. Read the Multi-Factor Authentication (MFA) How-to-Guide for more
information. - Utilize a password manager to remember all your long passwords. The most secure way to store all of your unique
passwords is by using a password manager. With just one master password, a computer can generate and retrieve
passwords for every account that you have – protecting your online information, including credit card numbers and their
three-digit Card Verification Value (CVV) codes, answers to security questions, and more.
Identity Theft and Internet Scams
Today’s technology allows us to connect around the world, to bank and shop online, and to control our televisions, homes, and cars from our smartphones. With this added convenience comes an increased risk of identity theft and Internet scams. #BeCyberSmart on the Internet—at home, at school, at work, on mobile devices, and on the go.
DID YOU KNOW?
- The total number of data breaches reported in 2018 decreased 23% from the total number of breaches reported in
2017, but the reported number of consumer records containing sensitive personally identifiable information (PII) exposed
increased 126%. - Credit card fraud tops the list of identity theft reports in 2018. The Federal Trade Commission (FTC) received more than
167,000 reports from people who said their information was misused on an existing account or to open a new credit card
account. - Consumers reported $905 million in total fraud losses in 2017, a 21.6% increase over 2016.3
COMMON INTERNET SCAMS
As technology continues to evolve, cybercriminals will use more sophisticated techniques to exploit technology to steal your
identity, personal information, and money. To protect yourself from online threats, you must know what to look for. According
to the FTC, these are the top three kinds of threats reported in 2018:
- Identity theft is the illegal acquisition and use of someone else’s personal information to obtain money or credit. Signs of
identity theft include bills for products or services you did not purchase, suspicious charges on your credit cards, or new
accounts opened in your name that you did not authorize. - Imposter scams occur when you receive an email or call from a person claiming to be a government official, family member,
or friend requesting personal or financial information. For example, an imposter may contact you from the Social Security
Administration informing you that your Social Security number (SSN) has been suspended, in hopes you will reveal your SSN
or pay to have it reactivated. - Debt Collection scams occur when criminals attempt to collect on a fraudulent debt. Signs the “debt collector” may be a
scammer are requests to be paid by wire transfers or credit cards. In 2018 there was a spike in requests for gift cards and
reloadable cards as well.
SIMPLE TIPS TO PROTECT IT.
- Double your login protection. Enable multi-factor authentication (MFA) to ensure that the only person who has access to
your account is you. Use it for email, banking, social media, and any other service that requires logging in. If MFA is an
option, enable it by using a trusted mobile device, such as your smartphone, an authenticator app, or a secure token—a
small physical device that can hook onto your key ring. Read the Multi-Factor Authentication (MFA) How-to-Guide for more
information. - Shake up your password protocol. According to NIST guidance, you should consider using the longest password or
passphrase permissible. Get creative and customize your standard password for different sites, which can prevent cyber
criminals from gaining access to these accounts and protect you in the event of a breach. Use password managers to
generate and remember different, complex passwords for each of your accounts. Read the Creating a Password Tip Sheet
for more information. - Be up to date. Keep your software updated to the latest version available. Maintain your security settings to keeping your
information safe
PROTECT YOURSELF FROM ONLINE FRAUD
Stay Protected While Connected: The bottom line is that whenever you’re online, you’re vulnerable. If devices on your
network are compromised for any reason, or if hackers break through an encrypted firewall, someone could be eavesdropping
on you—even in your own home on encrypted Wi-Fi.
- Practice safe web surfing wherever you are by checking for the “green lock” or padlock icon in your browser bar—this
signifies a secure connection. - When you find yourself out in the great “wild Wi-Fi West,” avoid free Internet access with no encryption.
- If you do use an unsecured public access point, practice good Internet hygiene by avoiding sensitive activities
(e.g., banking) that require passwords or credit cards. Your personal hotspot is often a safer alternative to free Wi-Fi. - Don’t reveal personally identifiable information such as your bank account number, SSN, or date of birth to unknown
sources. - Type website URLs directly into the address bar instead of clicking on links or cutting and pasting from the email.
E-Commerce
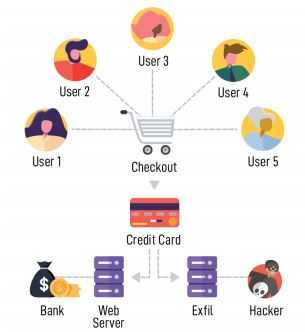
The Internet touches almost all aspects of our daily lives. We are able to shop, bank, connect with family and friends, and handle our medical records all online. These activities require you to provide personally identifiable information (PII) such as your name, date of birth, account numbers, passwords, and location information. #BeCyberSmart when sharing personal information online to reduce the risk of becoming a cybercrimes victim.
WHAT IS IT?
Cyber criminals introduce skimming code on e-commerce payment card
processing web pages to capture credit card and personally identifiable
information and send the stolen data to a domain under their control.
HOW DOES IT WORK?
Skimming code is introduced to payment card processing websites by:
- Exploiting a vulnerability in the website’s e-commerce platform
- Gaining access to the victim’s network through a phishing email or brute
force of administrative credentials - Compromising third-party entities and supply chains by hiding skimming
code in the JavaScript loaded by the third-party service onto the victim
website - Cross site scripting which redirects customers to a malicious domain
where malicious JavaScript code captures their information from the
checkout page
The malicious code captures credit card data as the end user enters it in real time. The information is then sent to an Internet-connected server using a domain name controlled by the actor. Subsequently, the collected credit card information is either sold or used to make fraudulent purchases.
WHO IS BEING TARGETED?
Any business accepting online payments on their website is at risk of an e-Skimming attack. This threat has impacted
e-commerce companies in the retail, entertainment, and travel industries as well as utility companies and third-party
vendors. E-Skimming is also commonly targeting third-party vendors such as those who provide online advertisements and
web analytics. The cyber criminals are evolving their tactics and have also been seen using malicious code that targets user
and administrative credentials in addition to customer payment information.
Online Privacy
The Internet touches almost all aspects of our daily lives. We are able to shop, bank, connect with family and friends, and handle our medical records all online. These activities require you to provide personally identifiable information (PII) such as your name, date of birth, account numbers, passwords, and location information. #BeCyberSmart when sharing personal information online to reduce the risk of becoming a cybercrimes victim.
DID YOU KNOW?
- 64% of U.S. adults have noticed or been notified of a major data breach affecting their sensitive accounts or personal
data. - Roughly half of Americans (49%) feel that their personal information is less secure than it was five years ago.
- 58% of Americans age 50 and older are more likely to feel that their personal information has become less safe in recent
years: 58% of Americans in this age group express this opinion. - 69% of consumers believe companies are vulnerable to hacks and cyberattacks.
SIMPLE TIPS TO OWN IT.
- Double your login protection. Enable multi-factor authentication (MFA) to ensure that the only person who has access to
your account is you. Use it for email, banking, social media, and any other service that requires logging in. If MFA is an
option, enable it by using a trusted mobile device, such as your smartphone, an authenticator app, or a secure token—a
small physical device that can hook onto your key ring. Read the Multi-Factor Authentication (MFA) How-to-Guide for more
information. - Shake up your password protocol. According to NIST guidance, you should consider using the longest password or
passphrase permissible. Get creative and customize your standard password for different sites, which can prevent cyber
criminals from gaining access to these accounts and protect you in the event of a breach. Use password managers to
generate and remember different, complex passwords for each of your accounts. Read the Creating a Password Tip Sheet
for more information. - Be up to date. Keep your software updated to the latest version available. Maintain your security settings to keeping your
information safe by turning on automatic updates so you don’t have to think about it, and set your security software to run
regular scans. - If you connect, you must protect. Whether it’s your computer, smartphone, game device, or other network devices,
the best defense against viruses and malware is to update to the latest security software, web browser, and operating
systems. Sign up for automatic updates, if you can, and protect your devices with anti-virus software. Read the Phishing
Tip Sheet for more information.
Social Media
Now more than ever, consumers spend increasing amounts of time on the Internet. With every social media account you sign up for,
every picture you post, and status you update, you are sharing information about yourself with the world. How can you be proactive
to stay safe online and, “Own IT. Secure IT. Protect IT.”? #BeCyberSmart and take these simple steps to connect with confidence
and safely navigate the social media world.
DID YOU KNOW?
- 3.48 billion people worldwide now use social media worldwide. That’s an increase of 9% from 2018. Put another way:45% of the total world population are using social networks.
- Digital consumers spend nearly 2.5 hours on social networks and social messaging every day.
- 69% of U.S. adults use at least one social media site and the average American has 7.1 social media accounts.
SIMPLE TIPS TO OWN IT.
- Remember, there is no ‘Delete’ button on the Internet. Share with care, because even if you delete a post or picture from your
profile seconds after posting it, chances are someone still saw it. - Update your privacy settings. Set the privacy and security settings to your comfort level for information sharing. Disable
geotagging, which allows anyone to see where you are—and where you aren’t—at any given time. - Connect only with people you trust. While some social networks might seem safer for connecting because of the limited
personal information shared through them, keep your connections to people you know and trust. - Never click and tell. Limit what information you post on social media—from personal addresses to where you like to grab coffee.
What many people don’t realize is that these seemingly random details are all that criminals need to know to target you, your
loved ones, and your physical belongings—online and in the real world. Keep Social Security numbers, account numbers, and
passwords private, as well as specific information about yourself, such as your full name, address, birthday, and even vacation
plans. Disable location services that allow anyone to see where you are—and where you aren’t—at any given time. Read the
Social Media Cybersecurity Tip Sheet for more information. - Speak up if you’re uncomfortable. If a friend posts something about you that makes you uncomfortable or you think is
inappropriate, let him or her know. Likewise, stay open-minded if a friend approaches you because something you’ve posted
makes him or her uncomfortable. People have different tolerances for how much the world knows about them, and it is important
to respect those differences. Don’t hesitate to report any instance of cyberbullying you see. - Report suspicious or harassing activity. Work with your social media platform to report and possibly block harassing users.
Report an incident if you’ve been a victim of cybercrime. Local and national authorities are ready to assist you.
Cyber Security While Traveling
In a world where we are constantly connected, cybersecurity cannot be limited to the home or office. When you’re traveling— whether domestic or international—it is always important to practice safe online behavior and take proactive steps to secure Internet-enabled devices. The more we travel, the more we are at risk for cyberattacks. #BeCyberSmart and use these tips to connect with confidence while on the go.
SIMPLE TIPS TO OWN IT.
Before You Go
- If you connect, you must protect. Whether it’s your computer, smartphone, game device, or other network devices,
the best defense against viruses and malware is to update to the latest security software, web browser, and operating
systems. Sign up for automatic updates, if you can, and protect your devices with anti-virus software. Read the Phishing Tip
Sheet for more information. - Back up your information. Back up your contacts, financial data, photos, videos, and other mobile device data to another
device or cloud service in case your device is compromised and you have to reset it to factory settings. - Be up to date. Keep your software updated to the latest version available. Maintain your security settings to keeping your
information safe by turning on automatic updates so you don’t have to think about it, and set your security software to run
regular scans. - Keep it locked. Lock your device when you are not using it. Even if you only step away for a few minutes, that is enough
time for someone to steal or misuse your information. Set your devices to lock after a short time and use strong PINs and
passwords. Read the Creating a Password Tip Sheet for more information. - Double your login protection. Enable multi-factor authentication (MFA) to ensure that the only person who has access to
your account is you. Use it for email, banking, social media, and any other service that requires logging in. If MFA is an
option, enable it by using a trusted mobile device, such as your smartphone, an authenticator app, or a secure token—a
small physical device that can hook onto your key ring. Read the Multi-Factor Authentication (MFA) How-to-Guide for more
information.
During Your Trip
- Stop auto connecting. Some devices will automatically seek and connect to available wireless networks or Bluetooth
devices. This instant connection opens the door for cyber criminals to remotely access your devices. Disable these
features so that you actively choose when to connect to a safe network. - Stay protected while connected. Before you connect to any public wireless hotspot—such as at an airport, hotel, or
café—be sure to confirm the name of the network and exact login procedures with appropriate staff to ensure that the
network is legitimate. If you do use an unsecured public access point, practice good Internet hygiene by avoiding sensitive
activities (e.g., banking) that require passwords or credit cards. Your personal hotspot is often a safer alternative to free
Wi-Fi. Only use sites that begin with “https://” when online shopping or banking. - Play hard to get with strangers. Cyber criminals use phishing tactics, hoping to fool their victims. If you’re unsure who an
email is from—even if the details appear accurate—or if the email looks “phishy,” do not respond and do not click on any
links or attachments found in that email. When available use the “junk” or “block” option to no longer receive messages
from a particular sender. Read the Phishing Tip Sheet for more information. - Never click and tell. Limit what information you post on social media—from personal addresses to where you like to grab
coffee. What many people don’t realize is that these seemingly random details are all that criminals need to know to target
you, your loved ones, and your physical belongings—online and in the real world. Keep Social Security numbers, account
numbers, and passwords private, as well as specific information about yourself, such as your full name, address, birthday,
and even vacation plans. Disable location services that allow anyone to see where you are—and where you aren’t— at any
given time. Read the Social Media Cybersecurity Tip Sheet for more information. - Guard your mobile device. To prevent theft and unauthorized access or loss of sensitive information, never leave your
equipment—including any USB or external storage devices—unattended in a public place. Keep your devices secured in
taxis, at airports, on airplanes, and in your hotel room.
Cyber Secure at Work
Businesses face significant financial loss when a cyber attack occurs. In 2018, the U.S. business sector had the largest number of data breaches ever recorded: 571 breaches. Cybercriminals often rely on human error—employees failing to install software patches or clicking on malicious links—to gain access to systems. From the top leadership to the newest employee, cybersecurity requires the vigilance of everyone to keep data, customers, and capital safe and secure. #BeCyberSmart to connect with confidence and support a culture of cybersecurity at your organization.
SIMPLE TIPS TO SECURE IT.
- Treat business information as personal information. Business information typically includes a mix of personal and
proprietary data. While you may think of trade secrets and company credit accounts, it also includes employee personally
identifiable information (PII) through tax forms and payroll accounts. Do not share PII with unknown parties or over
unsecured networks. - Technology has its limits. As “smart” or data-driven technology evolves, it is important to remember that security
measures only work if used correctly by employees. Smart technology runs on data, meaning devices such as
smartphones, laptop computers, wireless printers, and other devices are constantly exchanging data to complete tasks.
Take proper security precautions and ensure correct configuration to wireless devices in order to prevent data breaches.
For more information about smart technology see the Internet of Things Tip Card. Read the Internet of Things Tip Sheet for
more information. - Be up to date. Keep your software updated to the latest version available. Maintain your security settings to keeping your
information safe by turning on automatic updates so you don’t have to think about it, and set your security software to run
regular scans. - Social media is part of the fraud toolset. By searching Google and scanning your organization’s social media sites,
cybercriminals can gather information about your partners and vendors, as well as human resources and financial
departments. Employees should avoid oversharing on social media and should not conduct official business, exchange
payment, or share PII on social media platforms. Read the Social Media Cybersecurity Tip Sheet for more information. - It only takes one time. Data breaches do not typically happen when a cybercriminal has hacked into an organization’s
infrastructure. Many data breaches can be traced back to a single security vulnerability, phishing attempt, or instance
of accidental exposure. Be wary of unusual sources, do not click on unknown links, and delete suspicious messages
immediately. For more information about email and phishing scams see the Phishing Tip Sheet.
 Copyright © 2024
Copyright © 2024
Seamen's Bank
NMLS ID# 419878
Routing# 211373461

Privacy Notice
Electronic Funds Disclosure
Member FDIC · Member DIF
All accounts subject to approval
508.487.0035 local
855.227.5347 toll free
Career Opportunities!
